Hacker II
Your Rating: Not Yet Rated
Average Rating: 3.4 (7 people have rated this item.)
RAM Requirement: 512k RAM
Control: Mouse
Release Status: Abandonware
Year: 1987
Publisher: Activision
Developers: Steve Cartwright
System 6 Compatible: Yes
Hard Drive Installable: Yes
 Download 2image Archive (209k)
Download 2image Archive (209k)
 Download the manual in PDF format (5727k)
Download the manual in PDF format (5727k)
All ebay results related to this archive:
Hacker Apple II Game on 5.25" disk - Tested
Original Hacker II Disk by Activision for Apple IIGS
Apple Inside Macintosh, Volumes I, II, and III by Rose, Caroline|Hacker, Brad…
Hacker II : The Doomsday Papers - Apple II - Activision 1986 - Complete in Box
Activision Hacker Apple II Computer Game Portfolio 5.25" Floppy Disk
Current Apple IIGS related Auctions Listed By Time Left:
Vintage Software Apple II IIe IIc IIgs RUSSIA The Great War in the East
LEGO TC Logo - Super Rare DACTA - APPLE IIe & IIgs - Interface Card & Cable 9767
Apple ADB Touchpad Mouse Mice Replacement for G5431 m1042 M2706 A9M0331 IIGS IIe
Phonics Prime Time 1.0 by MECC for Apple II+, Apple IIe, Apple IIc, Apple IIGS
Sound Tracks 1.0 by MECC for Apple II+, Apple IIe, Apple IIc, Apple IIGS
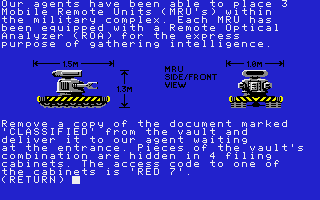
Hacker II was among Activision's first IIGS efforts, subsequently being one of the very first IIGS games being released to market.
Your hacking exploits have been recognised and respected by the CIA and you are enlisted for an assignment during one of your calls to a BBS. You are to infiltrate, remotely of course, a Russian secret base, which houses the Doomsday Papers; a set of papers to topple the American government. Your remote commands are relayed to 3 MRUs (remote control robots) to find and obtain the Doomsday Papers. Control of these robots is quite interesting, as you use a customised terminal, which also includes the features of displaying video input from the Russian base, or you can OUTPUT to the security cameras (or rather, output to whoever's watching them on the base) to send false images. These false images can be recorded by yourself through a security camera (preferably showing that none of your robots is in sight) and can be played back as output so that your robots can slip past security camera hotspots undetected.
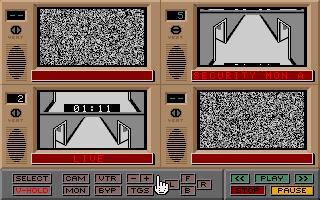
Before you enter the real game, you will have to ensure that you understand the equipment before you begin. This is not a form of copy protection, but provides interesting background information as to how the setup works. If you understand flow charts you can make some educated guesses as to what the answers are. After the diagram (key in the answers with the corresponding numbers on the keyboard), you are then presented with the terminal control screen and you will be quizzed as to what the different functions are (this is very useful, as you will learn what each button does). Luckily you won't have to go through this every time you play, as you are given a user name that's to be typed in at the terminal prompt to bypass that last section the next time you play. You use the mouse to play. It may look daunting at first, but half the fun is learning the terminal. You toggle between the four different monitors between you, and you can adjust the horizontal control and switch between the different security cameras with the CAM button. Learn control over your monitors before you start to move the first MRU.
Now it gets trickier. You must devise a way to keep visual track of your MRU and keep a look on the map (accessible from any monitor) AND keep a look out for the security guards on patrol who will sound the alert and your presence will be "disposed of". Good hunting of the Doomsday papers!
Hacker II is quite a clever game, its best feature being the customised terminal and the player having to master its controls. I can easily say that I've not progressed very far into Hacker II, but I'd say once you're hooked, you're hooked.




